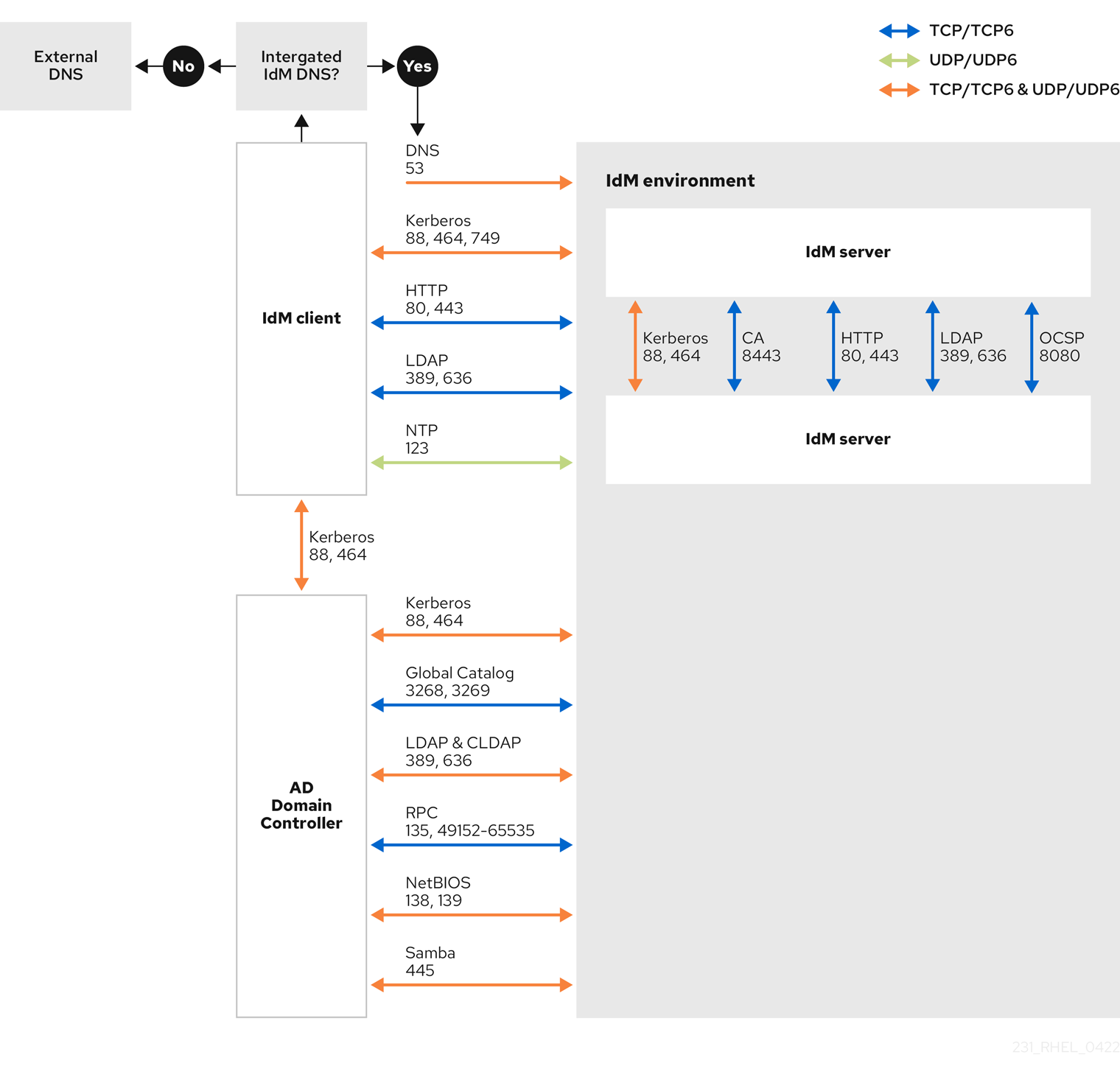
Chapter 6. Ports required for communication between IdM and AD Red Hat Enterprise Linux 9 | Red Hat Customer Portal

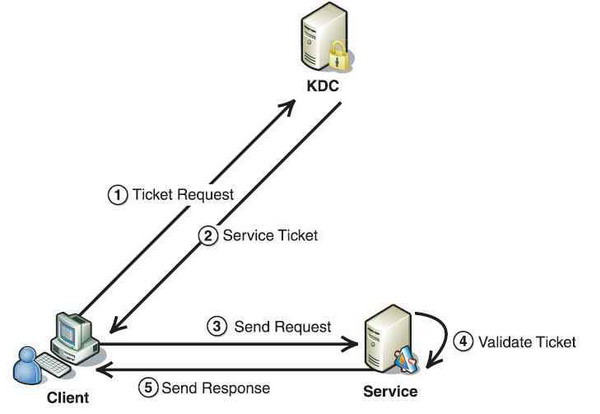
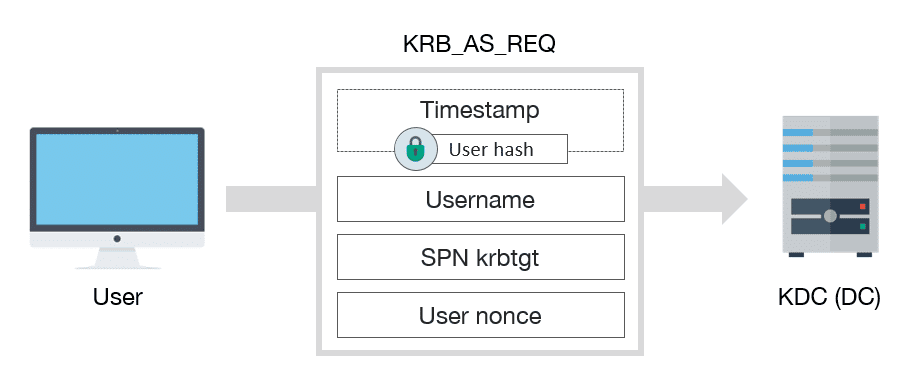
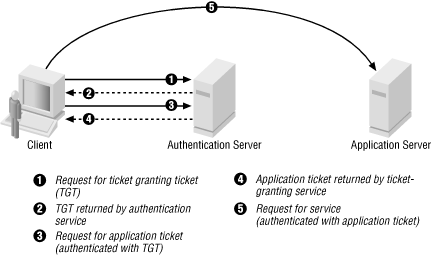
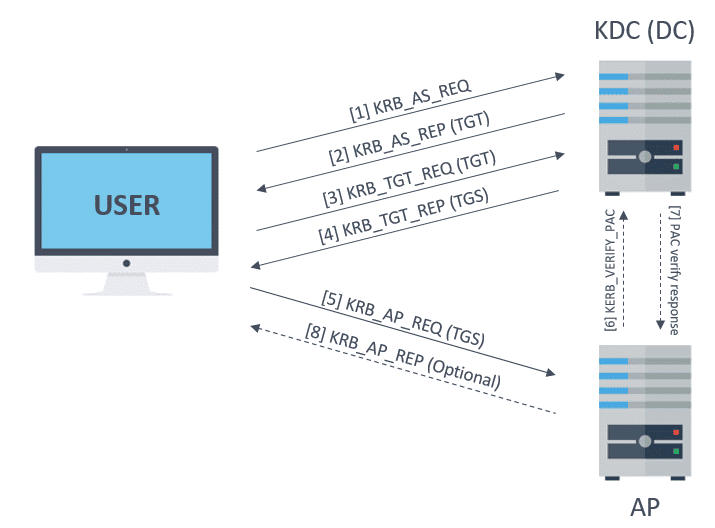
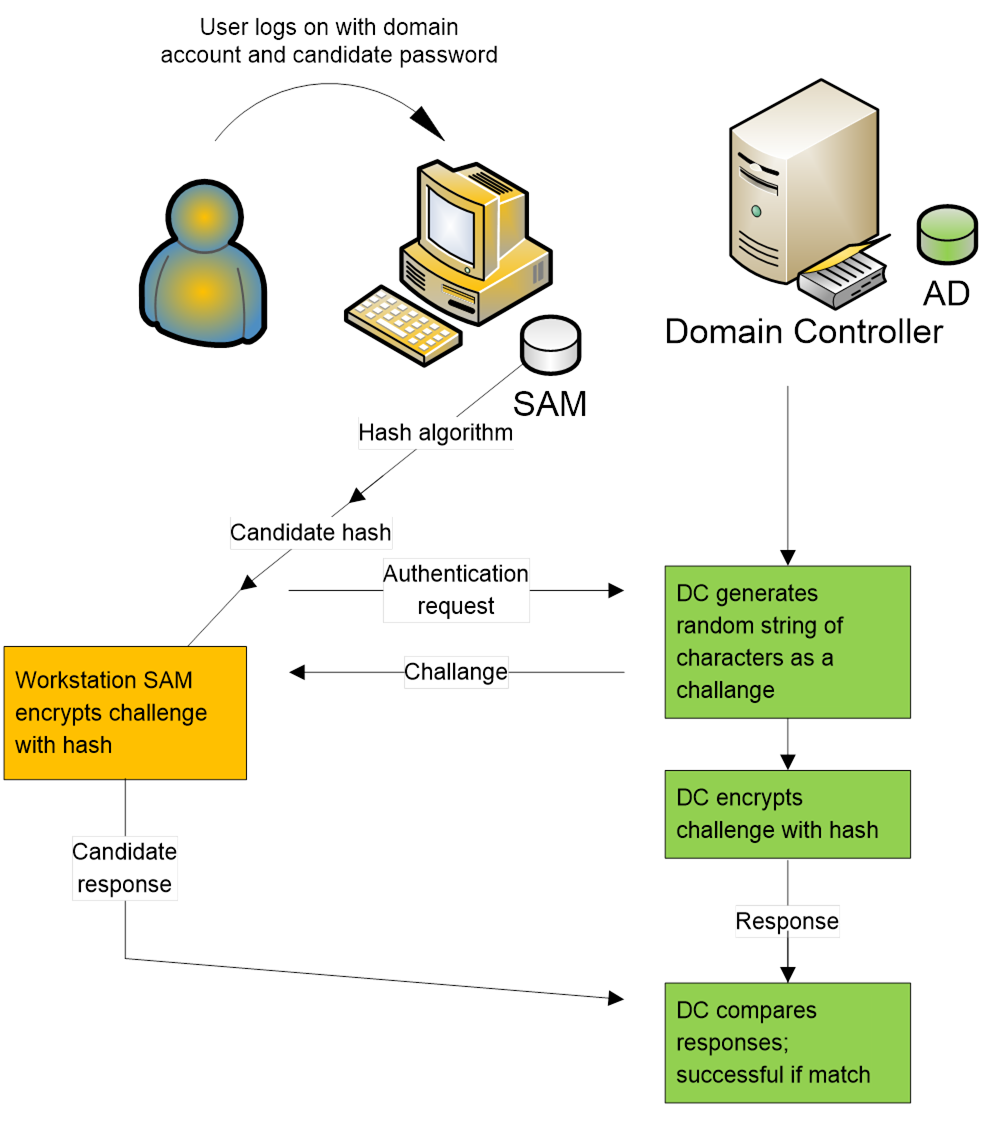
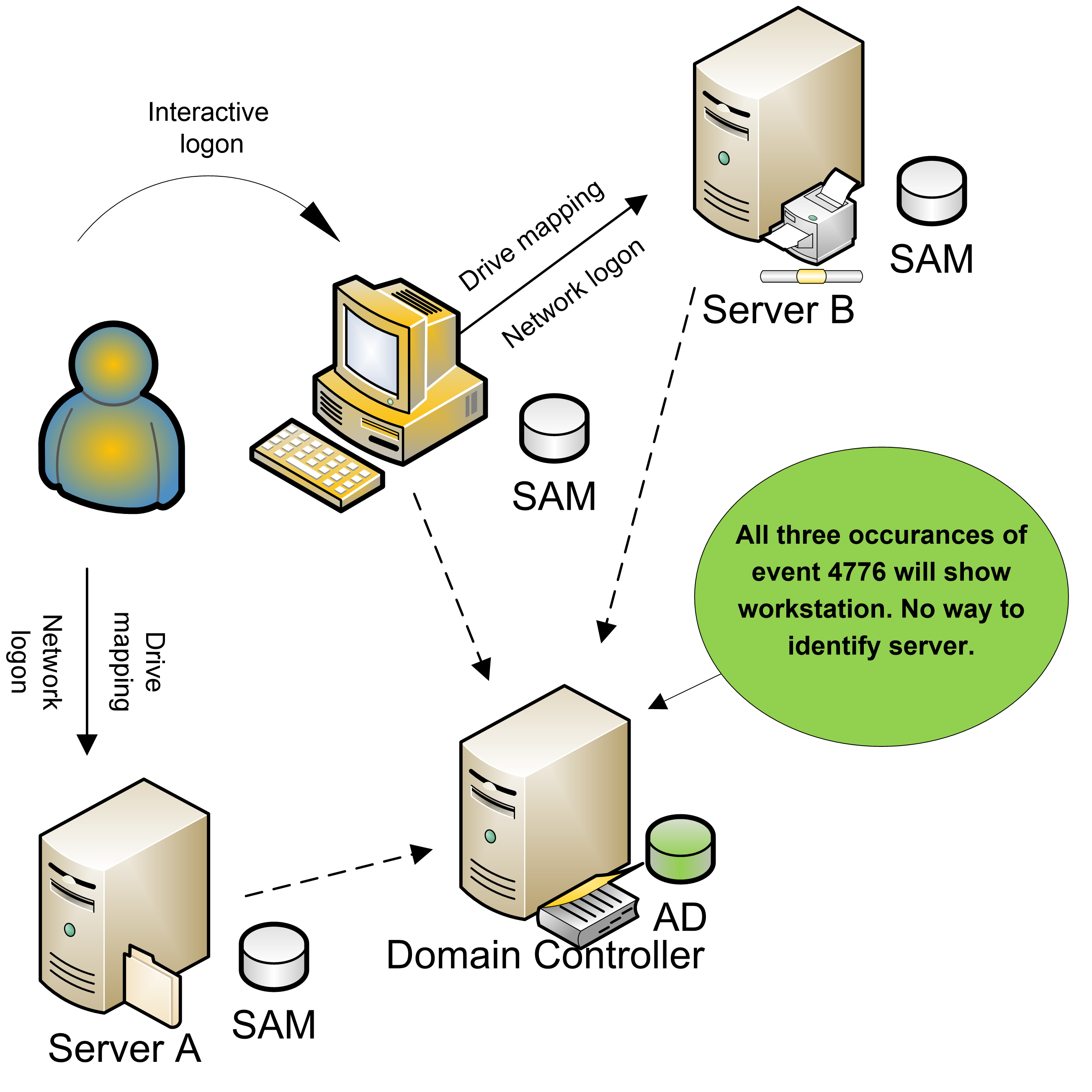
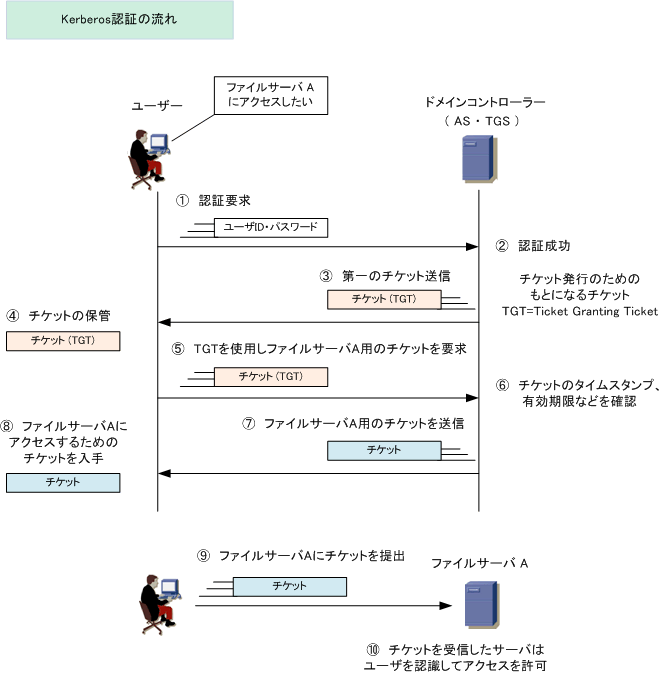
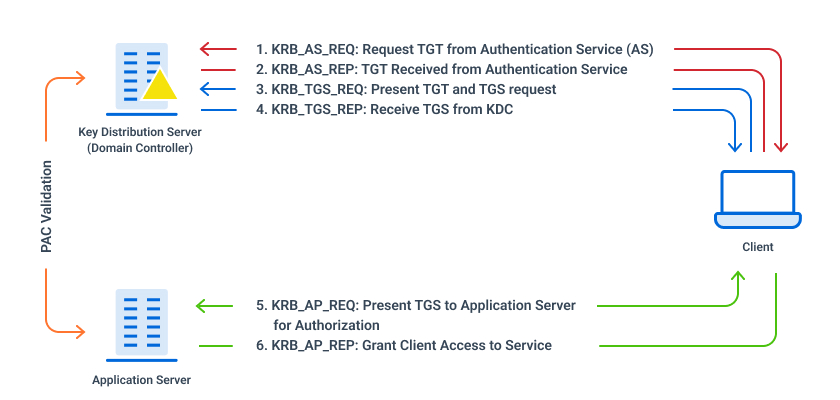
ECE Bayanihan Forum - General Infromation: Kerberos (Protocol) Kerberos is a computer network authentication protocol which works on the basis of "tickets" to allow nodes communicating over a non-secure network to prove