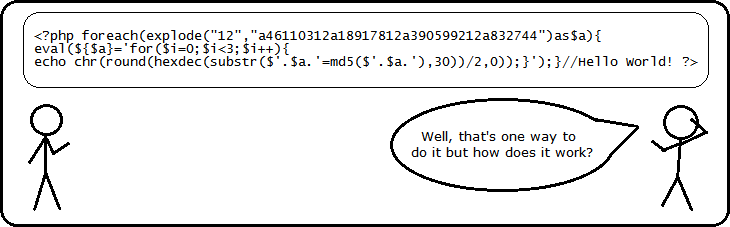
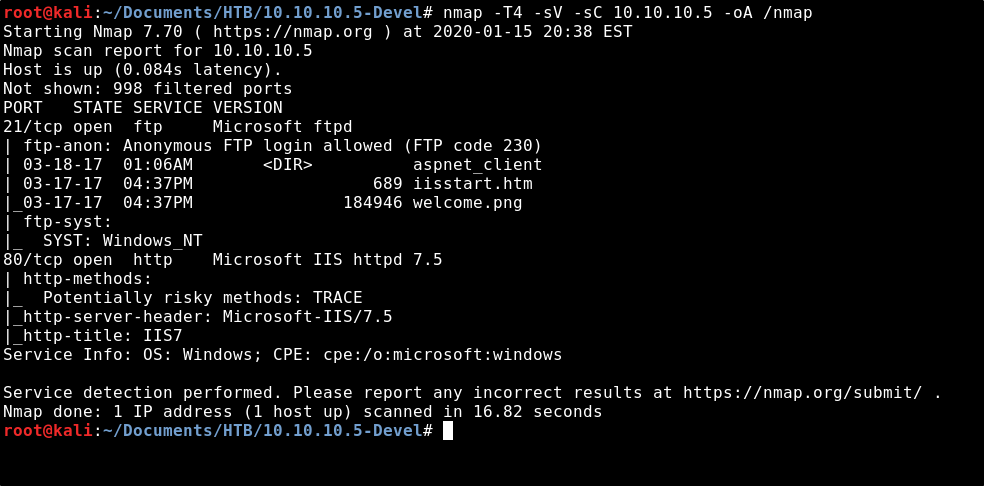
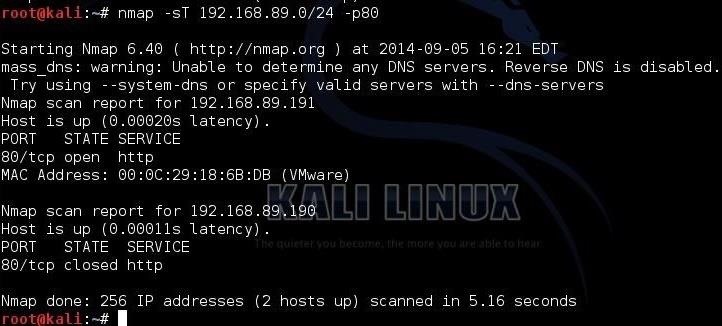
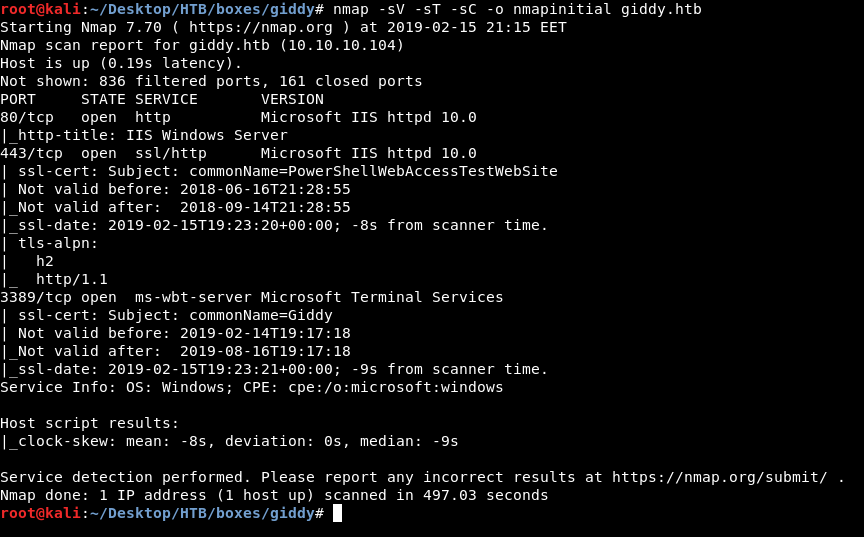
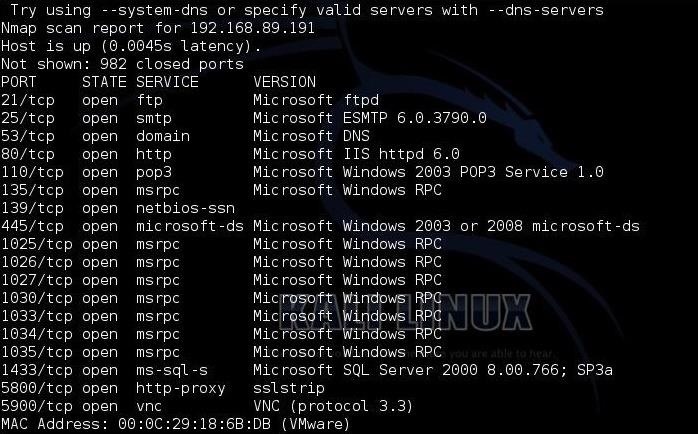
Metasploitable 2: Port 80. Welcome back to part IV in the… | by Miguel Sampaio da Veiga | Hacker Toolbelt | Medium
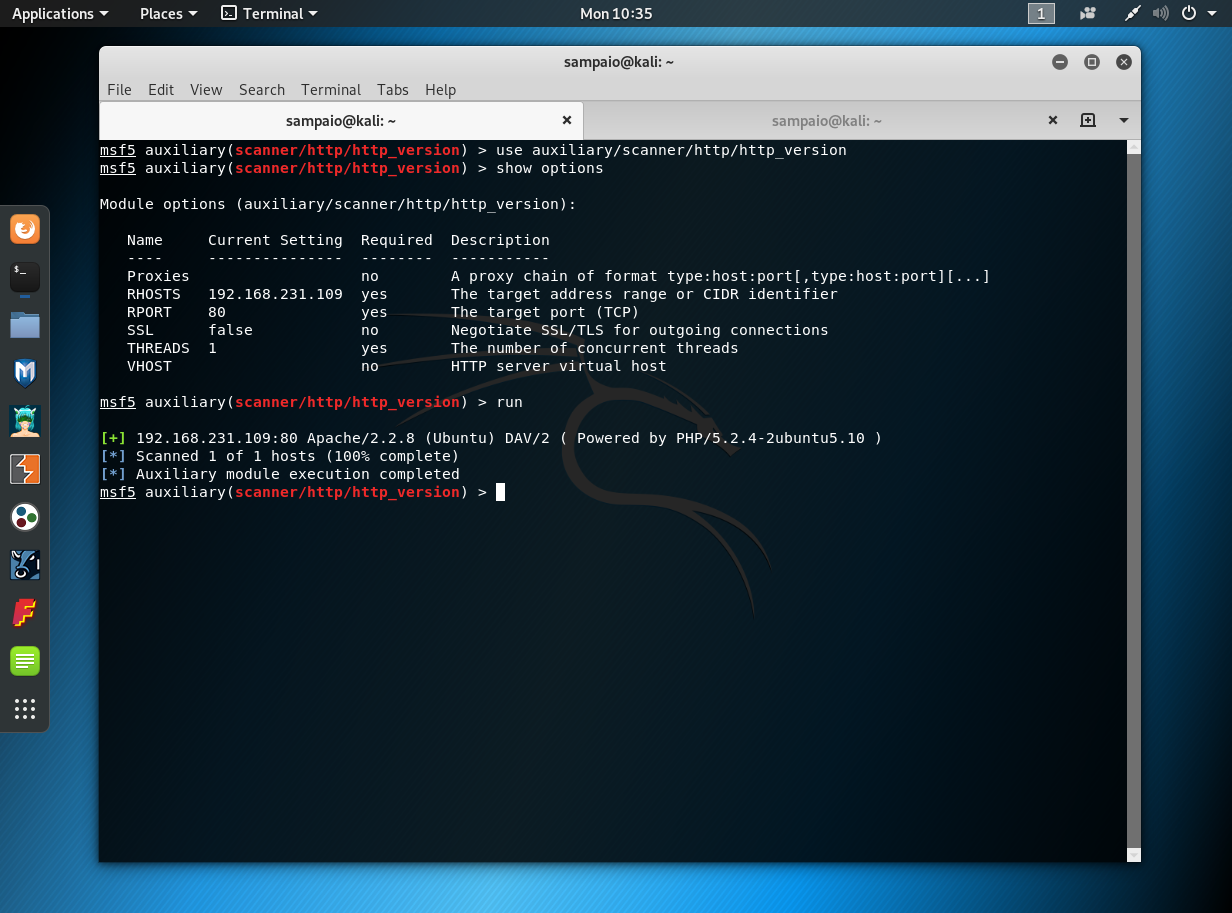
Metasploitable 2: Port 80. Welcome back to part IV in the… | by Miguel Sampaio da Veiga | Hacker Toolbelt | Medium
![Nothing is impossible.... Unless you want to hack someone over telnet on port 80 [humor] : r/hacking Nothing is impossible.... Unless you want to hack someone over telnet on port 80 [humor] : r/hacking](https://external-preview.redd.it/ezsQTkew7-7dfvD2xaIEesJmnDpO0LtIsSq8ZYKhGmM.jpg?auto=webp&s=d8d9f42087d686af7d35bff876e886b657c2c903)
Nothing is impossible.... Unless you want to hack someone over telnet on port 80 [humor] : r/hacking